In fact, in SharePoint 2016, the “FIM Sync” option no longer exists, so if you’re on SharePoint 2013 and still clinging to FIM Sync, you’ll need to start looking into either AD Import or an external identity manager like “Microsoft Identity Manager” (MIM) 2016. Here are some really good reasons for using AD Import. SharePoint 2010 and 2013 both use some parts of ForeFront Identity Manager (FIM) for the synchronization of users between for example AD and SharePoint. It is possible to use the FIM client to monitor this process and review issues related to the User Profile Service Application. The client application is located under the following folder. The scenario is that I am installing FIM 2010 R2 SP1 on Windows Server 2012. This means I will use SharePoint Foundation 2013 for my FIM Portal. I also use the same SQL Server as I use for my FIM Service but use a separate SQL alias for SPF in order to be able to easily move it if required. Unfortunately, the SharePoint site it pre-configures uses Claims-Based Authentication, which FIM doesn’t support, and to create a site that uses classic-mode Windows Authentication, you’re going to have to delete the pre-configured site and create a new one via the SharePoint 2013 Management Shell (not supported via the GUI). If you’re new to SharePoint, here are the directions to install SharePoint 2013 Foundation (I have no idea how SharePoint Server differs): 1) Click on the SharePoint installer (sharepoint.exe). 2) On the “SharePoint Foundation 2013” screen, click on “Install SharePoint Foundation”. 3) Follow the prompts through the wizard.
SharePoint 2013: Installing Your SSL Certificate
Microsoft SharePoint 2013 does not include a GUI for installing the SSL Certificate. Because SharePoint 2013 is designed to run on Microsoft IIS 8, you can use IIS. If you have not yet created a Certificate Signing Request (CSR) and ordered your certificate, see Microsoft SharePoint 2013: SSL Certificate CSR Creation Instructions.
The SharePoint SSL Certificate installation process consists of three steps:
Fim Service Sharepoint 2013
Installing the SSL Certificate
If you used IIS 8 to generate your CSR, you need to use IIS 8 to install the SSL Certificate,
See Using IIS 8 to Install the SSL Certificate.
If you used the DigiCert® Certificate Utility for Windows to generate your CSR, you need to use the DigiCert Certificate Utility to import/install your SSL Certificate.
See SSL Certificate Importing Instructions: DigiCert® Certificate Utility for Windows.
Assigning or binding the certificate to your SharePoint site
See Using IIS 8 to Assign the Certificate to the SharePoint Website.
Installing the root certificate
See Using SharePoint 2013 to Install the Root Certificate.


SharePoint 2013: How To Install Your SSL Certificate
Using IIS 8 to Install the SSL Certificate
After DigiCert validates and issues your SSL Certificate, you can use Microsoft IIS 8 to install your SSL Certificate to the server where you generated the CSR, and then, bind it the SharePoint site.
Save the SSL Certificate file (your_domain_name.cer) to the server on which the CSR was generated.
Open Internet Information Services (IIS) Manager.
From the Start screen, type and click Internet Information Services (IIS) Manager.
In Internet Information Services (IIS) Manager, under Connections, select your server’s Hostname.
In the center menu, in the IIS section, double-click the Server Certificates icon.
In the Actions menu, click Complete Certificate Request to open the Complete Request Certificate wizard.
On the Specify Certificate Authority Response page, under File name containing the certification authority’s response, click … to browse to the .cer certificate file that DigiCert sent you, select the file, and then, click Open.
Next, in the Friendly name box, enter a friendly name for the certificate. The friendly name is not part of the certificate; instead, it is used to identify the certificate.
We recommend that you add DigiCert and the expiration date to the end of your friendly name, for example: yoursite-DigiCert-expirationDate. This information helps identify the issuer and expiration date for each certificate. It also helps distinguish multiple certificates with the same domain name.
Next, in the Select a certificate store for the new certificate drop-down list, select Personal.
To install the SSL Certificate to the server, click OK.
Once you have successfully installed the SSL Certificate to the server, you still need use IIS to assign or bind that certificate to the SharePoint site.
Using IIS 8 to Assign the Certificate to the SharePoint Website
In Internet Information Services (IIS) Manager, under Connections, expand your server’s name, expand Sites, and then select the SharePoint site.
In the Actions menu, under Edit Site, click Bindings.
In the Site Binding window, click Add.
In the Add Site Bindings window, enter the following information:
Type: In the drop-down list, select https. IP address: In the drop-down list, select All unassigned. If your server has multiple IP addresses, select the one that applies. Port: Enter 443, unless you are using a non-standard port for SSL traffic. SSL certificate: In the drop-down list, select the friendly name of the certificate that you just installed. When you are finished, click OK.
Now you need to install the root certificate on your SharePoint server.
Using SharePoint 2013 to Install the Root Certificate
Log into the DigiCert® Management Console (your account).
In the DigiCert® Management Console, under Order, click the order number for the SSL Certificate that you just installed.
On the My Orders tab, click Download.
In the Download Certificate section, click the Download or Copy/Paste Individual Certificates link.
Next, click the ROOT CERTIFICATE icon.
In the Opening TrustedRoot.crt window, click Save File to save the file to your SharePoint server.
Next, open SharePoint 2013 Central Administration.
From the Start screen, type and click SharePoint 2013 Central Administration.
In SharePoint 2013 Central Administration, in the menu on the left, click Security and then, under General Security, click Manage trust.
On the Trust Relationships page, in the menu at the top of the page, click New.
In the Establish Trust Relationship window, in the General Setting section, in the Name box, type the name that you want to give the SSL Certificate.
In the Root Certificate for the trust relationship section, click Browse to browse for and select the root certificate (i.e. TrustedRoot.crt).
In the Establish Trust Relationship window, click OK.
If the certificate is installed successfully, it should be listed on the Trust Relationships page.
Test Your Installation
Fim Service Disabled Sharepoint 2013
If your web site is publicly accessible, our DigiCert® SSL Installation Diagnostics Tool can help you diagnose common problems.
Troubleshooting
If you run into certificate errors, try repairing your certificate trust errors using DigiCert® Certificate Utility for Windows. If this does not fix the errors contact support.
Additional Information
IIS 8 and Windows Server 2012 have the Server Name Indication-SNI feature, which you can use to host multiple SSL sites and certificates on a Single IP Address based on Host Headers on your IIS 8 server.
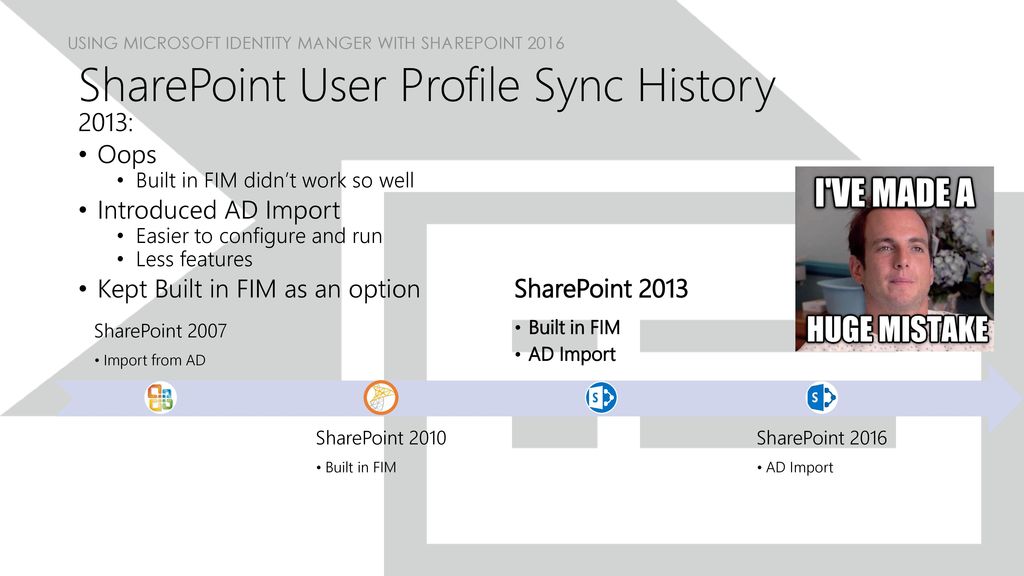
SharePoint 2010 and 2013 both use some parts of ForeFront Identity Manager (FIM) for the synchronization of users between for example AD and SharePoint. It is possible to use the FIM client to monitor this process and review issues related to the User Profile Service Application.
The client application is located under the following folder:
SharePoint 2010

C:Program FilesMicrosoft Office Servers14.0Synchronization ServiceUIShellmiisclient.exe
SharePoint 2013
C:Program FilesMicrosoft Office Servers15.0Synchronization ServiceUIShellmiisclient.exe
Unable to connect to the Synchronization Service
The following error can occur when opening the FIM Client:
The reasons described above are normally the correct steps to investigate this issue.
1) The service is not started.
There are 2 windows services that are related to FIM:
– Forefront Identity Manager Service
– Forefront Identity Manager Synchronization Service
These services have to be started before you can use the FIM client! You can start these services by going to the Central Administration of SharePoint and start the User Profile Synchronization Service.
Note that the Windows Service can still be stopped even if Central Administration shows that the service is started! Stop this service and start it again.
Please see the following blog from Spencer for other issues related to the User Profile Service Application: http://www.harbar.net/articles/sp2010ups.aspx
2) Your account is not a member of a required security group.
First verify if you can open the client using the farm account, because this service account has sufficient permissions.
The Admin account should have local admin permissions and located permissions in the Local Security Group “WSS_ADMIN_WPG”. Members of this group have write access to system resources used by Microsoft SharePoint Foundation.
Starting and monitoring multiple syncs
Sync with 2 new AD Users
I have added two new users to Active Directory and will start a new incremental Sync from the SharePoint User Profile Service Application. You can now open the FIM client and view the different syncs.
The DS_DELTAIMPORT shows the import from your Synchronization Connection and you will see more if you have multiple Connections.
There are 2 users added to SharePoint. Clicking on the number shows which users have been added.
Sync with 1 deleted and 1 changed user
I have deleted ‘Sync Test 2’ and changed the display name for ‘Sync Test 1’ to ‘Change test 1’. DS_DELTAIMPORT now shows the following information
You can also view the user that has been deleted by clicking on the number
You can also view the changed properties of the other user by using the MOSS_EXPORT_<GUID> profile and clicking on the number next to updates.
And clicking properties for this user
Searching users
Looking for a specific change may be time consuming when your organizations has thousands of users
You can use the Metaverse Search to find the user you are looking for and see if this user has been updated with the correct information.
You can filter the search on multiple attributes
My filter is for users which display name contains “Change”
You can then view the properties of this user
You can find the change by clicking on the connectors tab
And opening the connector “MOSS-<GUID>”
And find the latest sync on Lineage
You can troubleshoot further if the last import change is different from the latest sync. This normally happens when the user has been moved from the specified OU in Synchronization Connections.
Summarizing
You can now troubleshoot the error prompted when opening the FIM client and you can do basic monitoring of the specified syncs. You can find if a user has been updated to the latest AD information and when the user has last been updated.
